The character of war is changing. Before the end of this decade, the United States and its allies will face a new kind of warfare. Advanced and emerging technologies, including artificial intelligence, combined with operational concepts that harness them in innovative and unexpected ways, are creating new ways to apply military force. America’s principal rival, China, is harnessing these changes with the aim of eroding or even leapfrogging the United States’ military strengths. Meanwhile, the brittleness of America’s defense industrial base, the slow transition in U.S. military capabilities from a small number of exquisite legacy systems to many lower-cost, innovative systems, and the struggle to shift from traditional operational concepts compound these challenges. The stakes could not be higher. If the United States does not rise to this challenge, the consequences could be dire: a shift in the balance of power globally, and a direct threat to peace and stability that the United States has underwritten for nearly 80 years in the Indo-Pacific – the most economically, technologically, and resource-critical region of this century.
The United States should respond neither with despair nor hubris. Throughout history, the American military has demonstrated an ability to employ military capabilities in new and innovative ways to confound adversaries. Moreover, the United States retains significant military-technological advantages that it can continue to leverage. Where our military overmatch has been compromised, we can rebuild it. Where our self-confidence has been shaken, we can regain it. But it will require decisive action now to reverse the ongoing erosion of U.S. military advantage.
We contend that by pursuing the Offset-X strategy, which should form the framework
for the next National Defense
Authorization Act, the U.S.
military would be better
prepared and positioned to outsmart, outpace, outmaneuver, and — as necessary — outgun the People’s Liberation Army.
This chapter outlines a technology-centered strategic approach the United States should pursue to begin accomplishing this. We start by describing how the character of conflict has changed and is expected to change over the next several years and what the U.S. military — and the country — must do to prepare for the coming changes. We explain how China aspires to defeat the United States in conflict. We then identify existing U.S. military-technological strengths that can be leveraged to create advantages that will be difficult for China to quickly duplicate. We conclude by outlining a new approach — what we term an Offset-X1 strategy — that could begin to lay the groundwork for the United States to circumvent China’s military advancements and thwart its theories of victory, restore America’s ability to more freely project power in the Indo-Pacific region, and position the United States to honor its commitments to the stability of the region.
The approach we propose can achieve these aims by pursuing primacy in situational awareness, by optimizing the collaboration and teaming between the United States’ highly trained servicemembers and machines, by turning China’s wide geographical exposure and oppressive domestic political control into an American advantage, by creating better software and the ability to adapt it more quickly, and by further empowering leaders at the lowest tactical levels. We contend that by pursuing the Offset-X strategy, which should form the framework for the next National Defense Authorization Act, the U.S. military would be better prepared and positioned to outsmart, outpace, outmaneuver, and — as necessary — outgun the People’s Liberation Army.
Changing Conflict and Warfare
New military capabilities, their novel application, and intensifying geopolitical rivalry are changing the very character of war and peace. We already see the emergence of this changing character in Ukraine. This new type of warfare will be shaped by both strategic and operational developments.
At the more strategic level, we see the following dynamics:
- Persistent conflict below the level of armed clashes. Repeated acts of aggression by authoritarian governments in China (and Russia), often enabled by advanced and emerging technologies, blur the lines between war and peace. These actions include frequent cyber-attacks, unrelenting disinformation operations, aggressive theft of intellectual property, and sabotage.2 Even if most of these actions are invisible to many Americans, they leave little doubt that the United States is now in a state of persistent conflict with Russia and China.
- The likelihood of war between great powers is rising. The blurring of lines between war and peace, acts of aggression by China and Russia, and the high stakes involved increase the risk of major war for the United States. Such a war would be unlike anything Americans have experienced. In the minds of many contemporary Americans, war has been something that happens elsewhere, with American forces experiencing relatively fewer casualties compared to past conflicts. Today’s technology changes that. The United States faces the growing threat of large-scale cyber-attacks on the homeland that could paralyze society, the disablement or destruction of space-based assets that underpin the economy and military operations, and even missile strikes on U.S. soil.
…the United States is now in a state of persistent conflict with Russia and China.
- Great power wars have the potential to devolve into protracted contests that place a high premium on the strength of the industrial base, innovation ecosystem, and political will. Knockout blows, decapitation strikes, and decisive battles rarely materialize in wars between great powers. Instead, great power adversaries are able to mobilize populations and resources in ways that cause wars to descend into long, grinding contests, in which political will and national resources play as large (or larger) a role as brilliant operational maneuver and deception. However, most Western economies – the United States included – lack the industrial capacity to rapidly replenish and sustain their forces. This includes the production of the necessary munitions, sensors, vessels, vehicles, and aircraft, possibly for months or even years into a conflict, as well as skilled personnel to produce them. The brittleness of the defense industry can become a serious strategic liability for the United States, presenting U.S. decision-makers with a tough dilemma of whether to escalate vertically or opt out of a conflict.
In addition to the resilience of the industrial base, the vibrancy and responsiveness of the innovation ecosystem to conflict requirements will also be key in a potential great power war of protracted nature. Quickly identifying, repurposing, and fielding new technologies and platforms could shift the tactical tide of war and prove to be of strategic importance. Finally, the industrial base and the innovation ecosystem, while necessary, are not sufficient. They are no substitute for political will to endure and persevere in a high-intensity and prolonged conflict. - Critical national infrastructure is vulnerable to cyber-attacks.3 Many critical sectors of American society and business are heavily reliant on digital systems and Internet connectivity that are not sufficiently secure; 2021 witnessed 649 reported incidents of ransomware attacks on entities within critical infrastructure sectors.4 This ever-expanding area of attack and its indispensable role make critical infrastructure an attractive target for offensive cyber-attacks. A large-scale attack would present serious challenges for our socio-economic functioning and ability to wage war.
- Adversaries’ applications of emerging technologies may not be ethically constrained. U.S. military operations will continue to be guided by U.S. and international law as well as the U.S. military’s regulations and ethical guidelines. However, America’s adversaries may not necessarily be guided by the same principles — as we see with the appalling actions of the Russian military in Ukraine. While China has not yet engaged in external military operations that have included emerging technologies in war, in a domestic law enforcement context their approach to data collection and the targeting of civilian populations in Xinjiang province raises fundamental concerns.5 China, in contrast to the U.S. military, has also not disclosed the existence or content of any regulations or policy directives that indicate how it intends to use emerging technologies in military operations in an ethically-responsible way. While the U.S. military should continue to follow law of war principles for its application of emerging technologies, it should not assume its adversaries will do the same – and it should be mindful of the advantages and disadvantages these differences create.
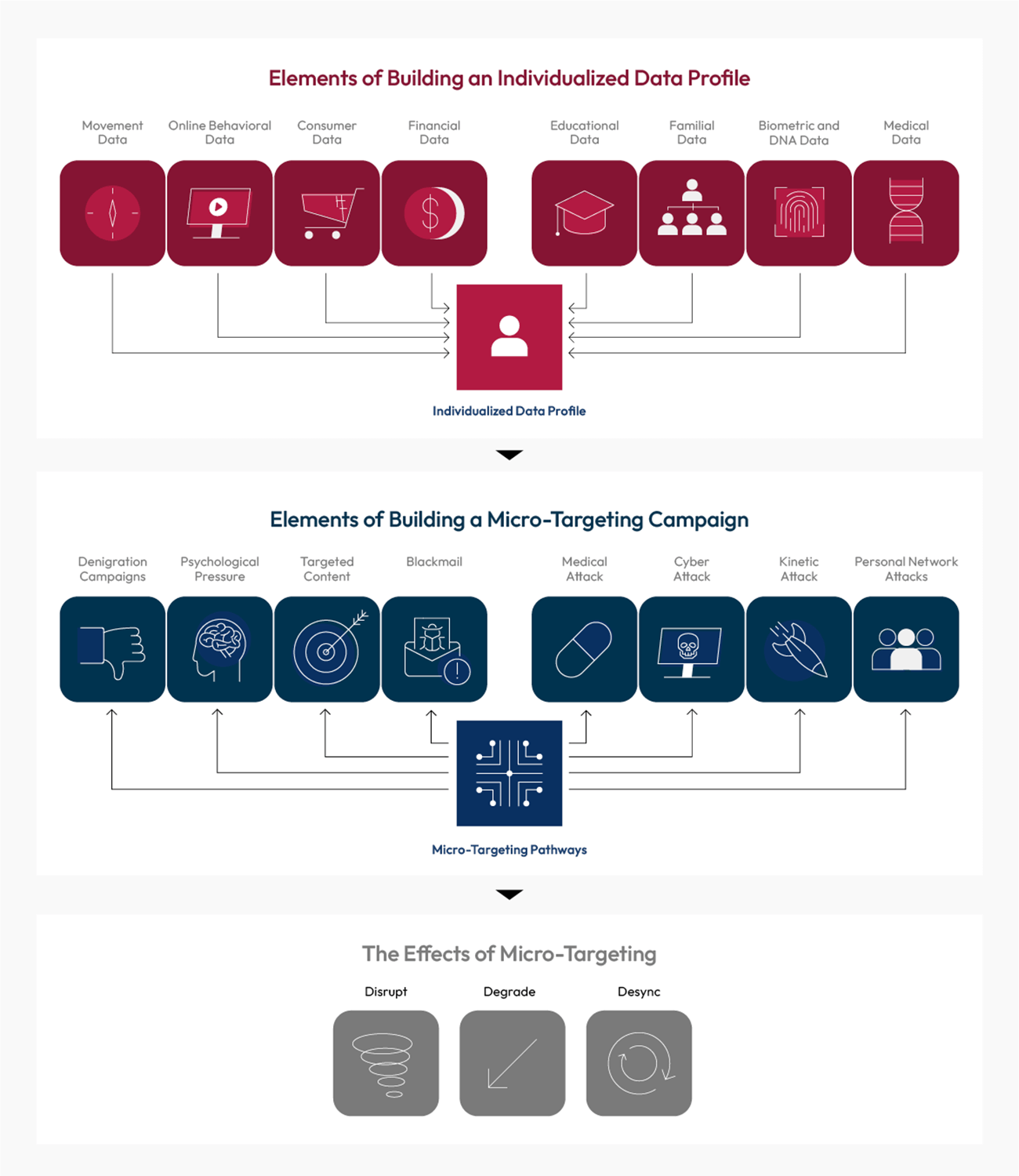
- The individualization of war. The proliferation of sensors, which collect the data exhaust that individuals leave on the Internet through everyday search, reading, watching, shopping, and dating habits, and the speed with which AI-enabled systems can analyze vast amounts of harvested data can position militaries to be able to micro-target individuals. This microtargeting is likely to entail, first and foremost, denigration campaigns and psychological pressure, but under certain circumstances could also entail targeting of key individuals with kinetic attacks. As we have seen in the Ukraine war, the Ukrainians have effectively and repeatedly tracked and targeted Russian military leaders.6 The effects can be delivered on the battlefield, close to it, or away from it. Individualization’s greatest threat is to peacetime and crisis decision-making, but it may also contribute to disrupting large-scale combat operations.
This individualization of war will change the psychology of war. On one hand, it creates the possibility of war with fewer casualties. On the other hand, the reach of new tech-enabled systems means that individual combatants, leaders, and even their family members are more easily targetable. When this takes place, anyone considered a target by the adversary will not be safe. U.S. service members, commanders, and policymakers will find themselves operating under persistent, individualized threats.
Individualization of war will also come about through further empowerment of individuals and small units who will have at their disposal increasingly more sophisticated technologies to deliver tactical to strategic effects. Individual service members are increasingly in control of a suite of strike or cyber platforms, both organic to the unit or that can be called upon to conduct an attack. As synthetic biology advances, more people can create pathogens, either from synthetic or naturally occurring DNA.7 By expanding the power of individuals, technology will increase uncertainty about which actions are taken by a state, by those acting on behalf of a state, or those acting on their own.
At the more operational level, we see the following dynamics:
- Emerging technology is qualitatively changing the way we perceive our environment, communicate, and make decisions. Mass data production and collection, behavioral tracking, and commercial imagery are increasing the availability of data for analysis, giving policymakers and military leaders much greater awareness. The application of AI and human-machine collaboration to this data will accelerate, diffuse, and compress decision-making to such an extent that at times it will seem almost instantaneous. AI can identify novel patterns and generate original insights. While cyber espionage can expose plans and intentions, increasing transparency, cyber operations can also deceive and defeat many sensors.
- The growing importance of software and connectivity will accelerate the adaptation of tactics and military technology. Lessons learned and software-based upgrades can be incorporated as quickly as programmers develop, transmit, and download new software. This allows software-based adaptation to bypass many of the physical and behavioral constraints of traditional adaptation. Over time, the combination of human insights and self-learning machines will allow extremely rapid changes to tactics and operating concepts.
- The proliferation of collection platforms,8 analytical tools, and precision-guided munitions are fundamentally altering the hider-finder contest. As these capabilities continue to develop and proliferate, it will become increasingly difficult to hide in every domain, including space and undersea that have traditionally been the most opaque. If adversaries more easily detect and rapidly destroy opposing forces while they are on the move, it will be difficult to employ operational surprise or tactics that rely on large formations consolidating or maneuvering, generally a key component of decisive victories. This trend will also drive a temptation for preemption, out of a desire to blind or immobilize the enemy. Restoring operational maneuver requires either subverting or overcoming enemy sensors, finding ways to restore the ability to surprise, or employing low-cost, attritable systems as part of an initial phase of operations to pave the way for subsequent attacks by regular formations.
- Relatively inexpensive drones and loitering munitions are already changing how militaries conceive of combined arms warfare. Drones played a prominent role in the 2020 Nagorno-Karabakh War by providing Azerbaijani forces with an aerial advantage against Armenian armor.10 Early reporting indicates drones played a similar role during the first phase of war in Ukraine,11 and loitering munitions have helped Ukrainian forces destroy light and armored targets cheaply from afar.12 Both conflicts have challenged the role that armor has traditionally played on the battlefield. As drone use in combat continues to advance and as autonomy improves, these systems will continue to change combat operations.
The People’s Liberation Army’s Theory of Victory to Defeat the U.S. Military
Over the last several decades, the United States has relied on its superior intelligence collection platforms, battle networks, and precision-guided and stand-off munitions to defeat adversaries. As adversaries develop similar capabilities, the ability of faster, more effective kill chains to realize military victory has diminished. Instead, warfare between great powers will increasingly see the confrontation of systems of sensors, networks, effects, and logistics.
For over two decades now, the PLA has closely studied the “American way of war” of guided munitions-battle networks warfare which they refer to as informatized warfare, and has worked relentlessly to adopt it for its own purposes. But the PLA has not only sought parity with the U.S. military in this regard. It has also developed a theory of victory centered around the idea of systems confrontation, whereby it would seek to destroy battle networks of its adversaries — which the PLA refers to as operational systems. This system destruction warfare aims to disrupt the flow of internal information, the time sequencing of control-attack-evaluation systems, and essential components of an adversary’s operational system through kinetic and non-kinetic means. PLA planners believe that immobilizing critical junctions in an opponent’s operational systems will isolate subsystems from critical resources and decrease overall system effectiveness.13 In short, they believe that military-technological parity in precision guided munitions-battle networks, and the application of their operating concept of system destruction warfare can lead them to military victory.14
In pursuit of a theory of victory for a potential confrontation today, the PLA has also sought to chart a path to leapfrog the United States for a potential confrontation of tomorrow. The PLA intends to capitalize on the growing capabilities of AI, big data, advanced computing, 5G, and supporting technologies to shift from informatized warfare to intelligentized warfare. By becoming the first movers in a new way of war, they hope to leapfrog the United States and become the world’s dominant military power. Intelligentization includes seven trends: (1) from the strong beating the weak to the intelligent beating the dull, (2) from destructive power to manipulating cognition, (3) from human-based to human-machine collaboration, (4) from big eats small to fast eats slow, (5) from winning through integration to winning through clusters, (6) from military dominance to hybrid warfare, and (7) from practical test to experimental exercise.15
The PLA’s weapon platforms and capabilities are also of increasing concern. The PLA has amassed a formidable, ever-expanding, arsenal of medium- and long-range precision missiles, including hypersonic missiles, capable of striking U.S. land and sea bases throughout the region and delaying or even preventing the United States from rapidly intervening in a crisis.16 The PLA has built a dense web of integrated air defense systems to challenge U.S. forces attempting to enter the theater of operations.17 The PRC also created the Strategic Support Force to merge information operations, including cyber, psychological operations, electronic warfare, and some space operations in an effort to operationalize system destruction warfare.18 In total, the PLA has focused on pursuing capabilities across all domains that challenge the U.S. military’s ability to project power into the Indo-Pacific region, or once there, to enjoy freedom of movement and action.
United States’ Asymmetric Strengths that Offer Opportunities for Advantages
While the magnitude of today’s challenges may be new, this is not the first time U.S. military primacy or its ability to project power has been called into question. Moreover, the U.S. military still enjoys considerable operational and military-technological asymmetries that can be leveraged against China, to include:
- Demonstrated Experience in Joint, Combined Arms, Expeditionary, and Networked Operations. Combined arms operations are highly complex and demanding. Twenty years of combat in Afghanistan and Iraq, along with demanding rotations at Combat Training Centers, Fleet Training Exercises, and Red Flag exercises have rendered these inherently complex operations familiar to the U.S. military.19 The PLA lacks the experience, trust, and cross-domain communication needed to effectively conduct joint and combined operations.20 It has, however, recognized these shortcomings and placed a high priority on making improvements.21
- Empowering Warfighters at the Lowest Tactical Levels. The inevitable chaos of modern warfare places a high premium on the ability to adapt rapidly to meet commander’s intent in the absence of regular guidance from higher headquarters.22 The U.S. military empowers its forces at the lowest level to take advantage of operational initiative and develop new solutions to fast-changing battlefield dynamics.23 The rigid structures of the PLA, and the conformist nature of its communist political system and society, typically do not promote or reward tactical initiative and rapid adaptation.24
- Expeditionary Logistics. The U.S. military-civilian logistics system has been one of America’s greatest military strengths, both in its reach and in its ability to sustain continuous operations. This stands in stark contrast, for example, with the Russian military, which has struggled to provide logistical support for its forces in Ukraine.25
However, since World War II, trans-continental and trans-regional logistics operations by the U.S. military have taken place in uncontested settings, often relying on commercial contractors to move assets and forces in a lengthy and unchallenged buildup process. By contrast, a conflict with China would likely see the PLA attack critical digital systems and physical operations in U.S. and foreign ports of embarkation and disembarkation and the logistics enterprise writ large. Such attacks could thwart the United States’ ability to maintain the flow of supplies to a complex conflict abroad, particularly if the U.S. military has not prepositioned sufficient materiel and forces in advance of a crisis. In short, the U.S. military has an impressive track record of conducting expeditionary logistics, but significant preparations need to be undertaken to retain this important advantage in the contested environment of an Indo-Pacific fight, where the vast distances involved, attacks on infrastructure, and the limited logistical throughput of the region can cripple operations. The PLA for its part has made efforts to strengthen its own untested expeditionary logistical capabilities.26 - Allies, Partners, and Global Posture. The United States has far more and much deeper alliances and partnerships than China, which has few or no allies. This advantage would enable the United States to generate greater diplomatic legitimacy, build military mass, create broader and deeper multi-domain effects, attack from different axes, and coordinate intelligence across a much larger network. The U.S. military’s expeditionary capabilities and consistent forward presence in key regions, particularly astride critical global choke points, further strengthen the U.S. global posture.27 This also makes it easier for the United States to rapidly deploy capabilities, employ military assets and forces, and sustain expeditionary logistics. At the same time, the United States military must be prepared for the possibility that not all allies or partners would join in a potential conflict with China, or even allow U.S. military forces to operate from their territories. Developing a more precise understanding of which nations may or may not grant U.S. access during wartime, and identifying those which are essential to U.S. military operations would mitigate some of the operational risks.
- The Strengths of a Democratic Society. Individual freedoms and empowerment — characteristic of democratic societies — foster innovation, entrepreneurship, and initiative. This makes the United States more resilient, agile, and more likely to adapt successfully to changing conditions. This empowerment of the individual and encouragement of initiative is also reflected in the U.S. military services. Additionally, the United States has deliberately pursued and built a professional and apolitical military force, which stands in stark contrast to the PLA. The PLA has a long history of corruption and coup-proofing.28 Both tendencies lead to promotions based on political loyalty rather than competency, a lack of trust in junior leaders, a lack of tactical initiative, an aversion to speaking truth to power, and ineffective decision-making due to less candid discussion during the planning process.29 They also contribute to the wasting of resources, and uncertainty in performance during conflict. These political constraints lead militaries to struggle to perform in chaotic conditions and during communication breakdowns, or to make significant, on-the-fly adjustments during combat missions. Phrased differently, in this system, regime security overrides national security.30 Authoritarian state stability relies on near total control, not resilience. Finally, China’s long-time pursuit of the one-child policy weakens its military strength.31 While the PLA will necessarily suffer a shortage of military personnel, any contingency that results in casualties will cause many families to lose their only child, resulting in considerable political blowback.
From Asymmetries to Advantages: An Offset-X Strategy
As we look towards 2025-2030, a war between great powers is more likely than it has been in generations. Emerging technologies are impacting the way militaries understand their environment and make decisions. Some of these same technologies will continue to change the tools of war, operational concepts, and how violence can be employed for political outcomes. While combat in traditional domains could still play a significant role, warfare will also be waged with and against industrial and financial power and pit innovation ecosystems against each other. It will be conducted across continents and borders and target individuals in new ways. It will be determined by political will as much as any other factor.
Over the last several decades, the United States has relied heavily on its superior intelligence collection assets, stand-off platforms, precision-guided munitions, highly-trained personnel, and expeditionary logistics to defeat adversaries. But advanced and emerging technologies are changing the reliability and effectiveness of these systems. Moreover, adversaries have developed some of the same capabilities, invested heavily in neutralizing America’s operational superiority, and focused on diminishing the ability of the U.S. military to employ faster, more effective kill chains. In this changing technological-military landscape, the PLA aims to, in a crisis or war, paralyze the U.S. body politic, bring America’s economy to a standstill, immobilize the U.S. military by destroying its battle networks, and present U.S. leaders with serious doubts about their ability to support partners and allies, leaving them with almost with no other option but to concede. Amid the uncertain overmatch for traditional U.S. military capabilities, the outcome of a potential war by the end of the decade with the PLA will increasingly come down to the superiority and resilience of sensors, networks, software, interfaces between humans and machines, logistics, and – especially – the systems that tie or empower them all together. It will also come down to the U.S. willingness and ability to insert itself now within the PLA’s envisioned future battlespace.32
In response to these challenges, we outline a new approach — an Offset-X strategy — that could lay the groundwork for the United States to restore its military-technological superiority, and in the process circumvent China’s military advancements, thwart its theories of victory, restore America’s ability to project power in the Indo-Pacific region, and position the United States to honor its commitments to the stability of the region. This approach is derived from and grounded in America’s persistent, asymmetric strengths, and envisions the deployment and employment of new capabilities in ways that China will struggle to match or quickly duplicate. It aims to minimize the human and political cost the United States and its allies would suffer during a war with China, while driving up the political costs of war and creating serious dilemmas for Chinese leadership.
The initiatives we outline below are, by no means, a comprehensive or definitive list of actions. Together, they embody a competitive strategy to achieve and maintain military-technical superiority over all potential adversaries. However, no offset strategy against China should be treated as set in stone. Rather, it needs to be regularly reassessed against the PLA’s adaptations, and should continuously seek to leverage emerging technologies. But we believe that the following initiatives provide a good starting point:
This approach is derived from and grounded in America’s persistent, asymmetric strengths, and envisions the deployment and employment of new capabilities in ways that China will struggle to match or quickly duplicate. It aims to minimize the human and political cost the United States and its allies would suffer during a war with China, while driving up the political costs of war and creating serious dilemmas for Chinese leadership.
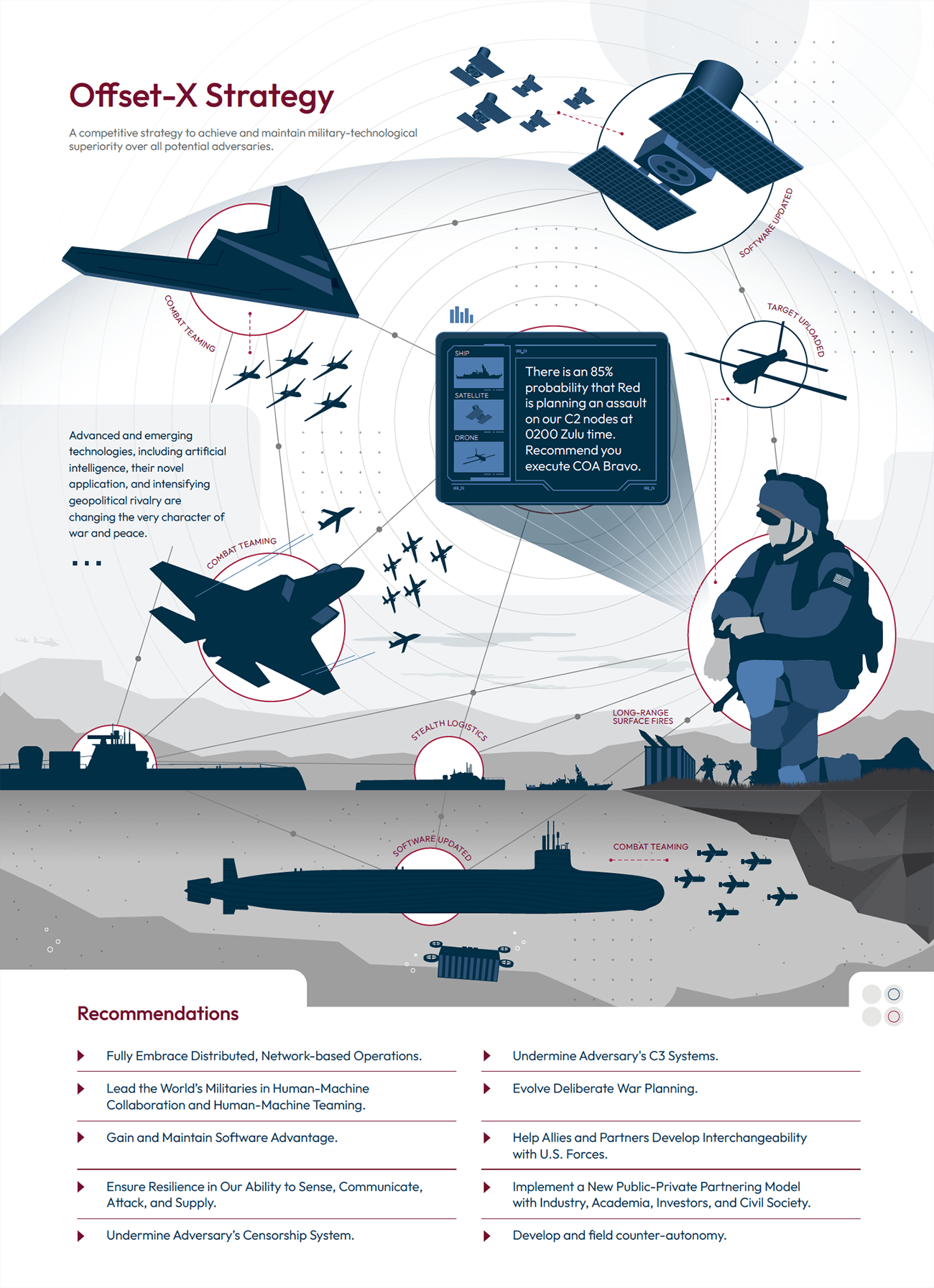
- Fully Embrace Distributed, Network-Based Operations to Survive, Out-Maneuver, and Overwhelm Adversaries. Confronted with adversaries that value rigid hierarchies and have invested in capabilities that could provide them with some protection against concentrated, frontal assaults, the U.S. military should continue to develop and experiment with how it will employ smaller, highly-connected, and organically resilient, multi-domain units that practice network-based decision-making and effects, not just hierarchy-based decision-making.33 Such units would operate in a distributed fashion, inside and outside an adversary’s envisioned battlespace. Such a network could generate significant dilemmas for the adversaries by creating multiple attack vectors and cross-domain effects. When acting in concert, distributed, networked forces can create mass, generate compounding effects, and operate with greater adaptability than single systems. When acting in isolation, they can distract and create new windows of operational opportunities, especially for follow-on, more conventional formations.
While the components of Offset-X strategy outlined here do not contain any recommendations on lethal autonomous weapon systems (LAWS), SCSP maintains that any application of emerging technologies for military purposes can and should be done in ways that are consistent with the laws of armed conflict. The U.S. Department of Defense has taken serious steps to ensure they have procedures and policies in place to responsibly field these capabilities.34
- Lead the World’s Militaries in Human-Machine Collaboration and Human-Machine Teaming. Essential to the concept of distributed, but highly-networked forces will be an extensive network of low-cost sensors, satellites, and reconnaissance platforms, as well as large numbers of attritable unmanned systems operating at sea, in the air, and on the ground to expand attack surfaces and absorb lethality. Employing them effectively, however, will require mastering human-machine cognitive collaboration (HMC) and human-machine combat teaming (HMT). HMC and HMT are assuming center stage in several states’ visions for the future of warfighting, and have the potential to considerably change warfare. For the U.S. military, human-machine cognitive collaboration will be critical to optimizing decision-making. Human-machine combat teaming, meanwhile, will be essential for more effective execution of complex tasks, especially higher-risk missions, or in confronting an adversary with sophisticated autonomous systems.
A core concept of HMC and HMT is that humans and machines have comparative advantages and therefore excel in different areas.35 Humans outperform machines on many sensory tasks, certain types of communication, high-context tasks requiring intuition, and various types of creative exploration. Machines often outperform humans at tasks that require processing extremely large volumes of data, a high degree of precision, memory, and consistent repetition. Augmenting human limitations with machine strengths (and vice versa), can create human-machine collaboration and teaming that outperform both humans and machines in many of their individual tasks. This may involve faster AI-powered decision-making, rapid processing and analysis of intelligence, surveillance, and reconnaissance (ISR) data, and combat tasking with autonomous systems, such as AI co-pilots.36 Also, machines are vastly better suited for high risk-to-force missions.
HMC focuses primarily on cognitive tasks. A warfighter’s mental bandwidth, as for every human, is limited. A decision to spend time solving one problem is a decision not to spend time on an equally critical task. The growth of HMC will enable individuals to break problems into their component pieces37 and task some to be optimized, automated, or performed at scale by a computer in order to remove some of the clutter that taxes so much cognitive energy and free that up for higher order processing. It will also allow individuals to refocus their mental bandwidth towards gaining situational awareness, understanding enemy plans, developing courses of action, accomplishing far more than they would otherwise, and mastering the tasks that humans do best.
Meanwhile, human-machine combat teaming could enable the U.S. military to generate and employ mass in contested environments and do so in a way that reduces the risk to humans,38 including risks of collateral damage. By employing lower-cost, easier-to-manufacture, and AI-enabled machines, new frameworks can be developed that leverage autonomy to permit operators and machines to overcome challenges of complexity so that what was once a single thing becomes a team of things. Single, expensive platforms cannot achieve the same diversity of use as swarms of inexpensive systems. Massed machines, assigned tasks by their human teammates, could overwhelm traditional defenses, often at a relatively smaller cost in human casualties compared to more traditional offensive operations. Machines could also serve as the “eyes and ears” of their human teammates, particularly in urban warfare, by helping them gain more information about their environment and taking risks in their place.
Another change that HMT can bring is in the balance of mass and effects delivery away from humans and towards machines. Today, in most cases, many warfighters collectively control one platform, such as a ship. While that relationship is unlikely to vanish, another human-machine relationship is developing that could begin to chip away at the dominant warfighter-platform relationship. One such mode is AI-powered architectures that leverage the contextual awareness and complex reasoning of human operators to manage large numbers of autonomous and semi-autonomous unmanned systems, as well as warfighters. An example of the potential of such an approach can be seen in DARPA’s OFFensive Swarm-Enabled Tactics (OFFSET) program.39
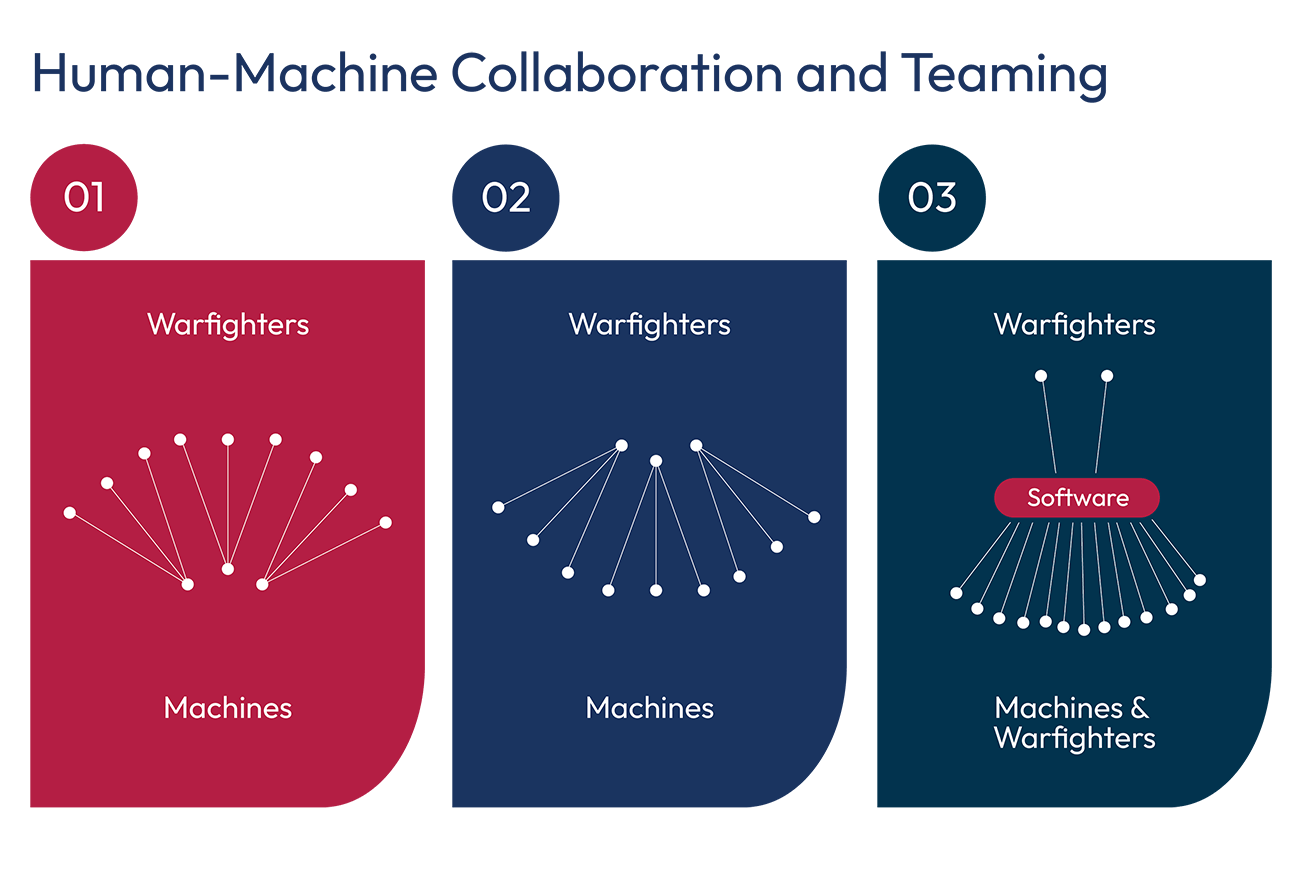
- HMC and HMT are not mutually exclusive concepts. Many applications, especially more advanced applications, will include elements of both. Also, while HMC and HMT are not analogous to autonomy, they will rely on autonomy for their effectiveness, especially during high-intensity conflicts. Autonomous systems can perform tasks assigned to them by human operators to increase or amplify U.S. military presence, persistence, and effectiveness, while reducing the risks and costs of operations, particularly in urban environments. HMC and HMT, thus, can serve as an engine of greater autonomy, where appropriate, by helping develop and test capabilities, human-machine interfaces, and the military’s ability to employ semi-autonomous or autonomous systems effectively and responsibly.
- By 2030, the U.S. military should fully integrate HMC and HMT into daily operations at the tactical, operational, and strategic levels. The military services should prioritize development, accelerate adoption, and integrate training on HMT in military schools and training centers. Combatant Commands should identify opportunities and take actions to integrate HMC and HMT into their operations at all levels, irrespective of progress at the level of services or Department. The near-term priority should be to develop the most sophisticated interfaces for HMC and HMT while exploring the degree of autonomy assigned to unmanned systems, consistent with U.S. Department of Defense policy and international law.
- Gain and Maintain Software Advantage. A military’s ability to deploy, employ, and update software, including AI models, faster than its adversaries is likely to become one of the greatest determining factors in relative military strength. Software is now integral to every component of decision and kill chains, from sensing a target (sensor software) to decision-making (aggregation and analysis), targeting (weapons guidance system), and battle damage assessment.40 The importance of software will only continue to increase. As militaries around the world increasingly rely on platforms with advanced computing capacities, and supplement or even replace some functions of human service members with algorithms, software superiority will become an even greater determining factor.41 The quality of software will determine a military’s ability to collect and analyze information, develop an operating picture, thwart enemy attacks, identify opportunities in time and space to most effectively attack, and help with target selection and servicing.
By 2030, the U.S. military should fully integrate HMC and HMT into daily operations at the tactical, operational, and strategic levels. The military services should prioritize development, accelerate adoption, and integrate training on HMT in military schools and training centers. Combatant Commands should identify opportunities and take actions to integrate HMC and HMT into their operations at all levels, irrespective of progress at the level of services or Department. The near-term priority should be to develop the most sophisticated interfaces for HMC and HMT while exploring the degree of autonomy assigned to unmanned systems, consistent with U.S. Department of Defense policy and international law.
Software already shapes how militaries organize, coordinate, and employ all of the elements of national power. Software can also facilitate a shift from a small number of very exquisite satellites to a large number of significantly less expensive and less capable systems, but whose integration through software can produce the same information as the existing, expensive satellites. Such a constellation of low-cost, space-based assets could also play a critical role in defending against missile attacks, particularly hypersonic missiles that challenge existing paradigms of in-flight tracking.
Similarly, the DoD also needs to adopt a new information architecture that will allow the DoD to be far more flexible, scale on demand, and adapt dynamically to changing conditions. As recommended by the National Security Commission on AI, this would include access to cloud computing and storage;42 a secure, federated system of data repositories with appropriate access controls; a secure network with the bandwidth needed to support data transport; common interfaces; development environments; and shared development resources that allow commands to quickly access the data, software, and models they need. The military also needs new specialties for tactical software development and management.43 At the operational and tactical levels, in order to more fully capture the power of software and accelerate its development, the U.S. military should empower its tactical units to experiment with, develop, and deploy robust, reliable, and resilient software for the capabilities that they operate. In short, the U.S. military should aim to develop every future system and capability with a software-centric orientation in mind. - Ensure Resilience in Our Ability to Sense, Communicate, Attack, and Supply. In a conflict with China, system destruction warfare would indicate that one of the PLA’s opening moves will be directed at U.S. forces’ ability to see them, listen to them, and locate them precisely. Simultaneous or follow-on attacks will likely target the ability of U.S. military leaders to command and control their forces. Additional attacks will almost certainly be aimed at the U.S. military’s ability to logistically sustain its operations. Blind, deaf, and unable to communicate, U.S. forces will be paralyzed.
To avoid this paralysis, the U.S. military needs to build resilience, and where necessary, redundancies across every link and node of its operations — from sensors to attack platforms, in information architecture and networks, across command and control, for logistics, and for humans. This includes both terrestrial and space-based systems and networks. Resilience can come from acquiring and using very large numbers of low-cost and attritable platforms that would support intelligence collection, communication, logistics, and attack — especially during the opening days of a campaign. And operational resilience will also require strategic resilience, which will be heavily dependent upon our ability to harden now the nation’s critical infrastructure from cyber-attacks. - Undermine Adversary’s Censorship System. Authoritarian regimes are brittle, relying more on information control than buy-in to maintain domestic stability. As such, they are vulnerable to operations that allow their populations to more easily and consistently bypass censorship systems and access information other than state propaganda. In the context of war, such operations — including AI-enabled messaging to circumvent censorship — have the potential to distract authoritarian regimes by increasing their focus on domestic security, to the detriment of their offensive operations. This would be especially important during a Chinese attempt to capture Taiwan by force. By helping ordinary Chinese citizens during times of war thwart automatic censors and by placing the burden on regime human censors, the United States can help expand the public discourse beyond the regime’s control.
- Undermine Adversary Command Systems. The United States should also consider how it can subvert the effectiveness of adversary command, control, and communication (C3) systems. If the United States were to disrupt or cripple the PLA’s C3 systems, it would cause disarray among the ranks of the PLA and desync its operations, preventing it from massing effects against U.S. forces. Preparing such offensively oriented operations, however, should be accompanied by defensive preparations. The U.S. military needs to be prepared, preferably with AI-enabled capabilities, to detect and defend against operations that flood our society with misinformation or undermine U.S. command, control, and communications systems.
- Evolve Deliberate War Planning. Traditionally, DoD’s deliberate war planning is based on the existing inventory of capabilities and forces. Planning guidance documents have generally instructed Combatant Commanders to construct war plans, and associated time-phased force deployments data (TPFDD), based on the capabilities available to them, in the first instance, and additional capabilities that could be allocated to them in the event of conflict from the total inventory.44
This approach to deliberate war planning, however, may no longer be suited for the anticipated changes in the character of warfare during this decade. First, the current method of planning does not factor in the state of the defense industrial base and its ability, or lack thereof, to surge production of munitions or platforms.45 This could result in serious strategic risks, particularly in the event of high-intensity operations that rapidly consume existing inventory of munitions and assets, or in the event of a protracted conflict. In other words, the current method of war planning runs the risk of producing a situation in which the U.S. military could run out of munitions or assets before reaching the end of conflict. Second, the resource straight-jacketing embedded in the current planning methods limits the development of innovative concepts and reduces the ability of Combatant Commanders to influence the development of new capabilities.
Put another way, Combatant Commanders are not encouraged to identify new disruptive technologies and develop corresponding concepts of operations that could lower the risk to force and mission. Therefore, the Defense Department should seriously consider evolving its deliberate war planning guidance documents and methodology, by considering the health and resilience of the defense industrial base and the full potential of the national security innovation network. This updated approach will likely result in plans that combine rigorous risk assessments with more effective operational solutions. This could also help DoD identify and prioritize the development and fielding of new, innovative capabilities. - Help Allies and Partners Develop and Maintain Interoperability and Interchangeability With U.S. Forces. As the United States continues to modernize its military forces, including investments in emerging technologies, there is a risk that a gap in capabilities between the United States and its allies could become a serious impediment to combined operations. Some of this gap is due to under-investments in defense by allies. Some of it has to do with security practices, particularly regarding the transfer of technologies, intelligence sharing, and command and control (C2) operations. But an important part of this gap also comes from the fact the United States has access to a unique innovation ecosystem. The United States must address these challenges if it is to capitalize on one of its most enduring asymmetries against China — the network of alliances and partnerships. In the near term, a promising action could be the establishment of a multilateral intelligence, surveillance, and reconnaissance network to improve coalition awareness in peacetime, and enable a more rapid transition from crisis to conflict during wartime.46 Another action could be the development of a Joint and Combined All Domain Command and Control (JCADC2) architecture. This would be the multilateral expansion of the current U.S.-only Joint All-Domain Command and Control (JADC2) concept.47 But the U.S. Government must accept far greater risks in information sharing and transfer of technologies to make this successful.
- Implement a New Public-Private Partnering Model Between the U.S. Government, Industry, Academia, Investors, and Civil Society. One of America’s greatest defense strengths in the past has been the close collaboration between the government, industry, and academia. That collaboration has, for various reasons, suffered over the past twenty years. At the same time, the CCP has been focusing on comprehensive national military-civil fusion.48 China continues its inexorable march toward reducing dependencies on the United States and advancing the development of Chinese technology companies. The United States must make a concerted effort to restore the level of collaboration between the government, industry, and academia, and to accelerate the adoption of commercial technology by the DoD. The defense industry played an essential role in developing capabilities that enabled the United States to prevail in the Cold War and conduct stability and counterterrorism operations in its aftermath and is already playing a critical role in the current geopolitical and technological contest. Just as importantly, collaboration must also extend to private investors and civil society. Civil society plays an important role in helping decide how technology should be employed, both for national security and civilian purposes. Private investors can bring to bear far greater capital towards the development and deployment of technology than the federal government. If the United States is able to unite all five stakeholders to pursue specific goals, America’s dynamic market capitalist system and innovative commercial sector is much more likely to prevail over the long term. If not, the United States risks ceding critical ground to China.
- Develop Counter-Autonomy. As the U.S. military integrates more AI, human-machine teaming, and autonomy, adversaries can be expected to do the same. The U.S. military should, therefore, develop capabilities and concepts for countering adversary autonomy. In the near term, the focus of U.S. counter-autonomy efforts could include identifying means and generating access to take over adversaries’ AI-enabled systems to extend our sensing deep inside their territory and within its decision-making. During conflict, counter-autonomy efforts could include actions to manipulate the data or outputs of adversarial AI-enabled systems so as to inject mistrust between their forces and their machines, degrading the performance of their AI-enabled and autonomous systems, or destroying them entirely through kinetic or non-kinetic means.49 While the immediate focus of the U.S. military should remain on developing its own autonomous systems, the United States cannot afford to wait for too long to develop the ability to counter and defeat adversarial AI-enabled and autonomous operations.
Operationalizing the Offset-X Strategy
The ten recommendations outlined above embody a competitive strategy to lay the groundwork for achieving and maintaining military-technical superiority over all potential adversaries. They are not intended as nor should be viewed as an operational prescription. Significant prototyping, experimenting, and wargaming will need to be undertaken to validate the applicability and effectiveness of various innovative technologies for specific operational demands. The precise mix of emerging technologies and capabilities will yet need to be determined to address the changing character of warfare and peace. But as with previous successful offset strategies, the national and DoD pursuit and mastery of emerging technologies and innovation can enable the crafting of new operational concepts that can be tailored to meet specific military challenges. Offset-X strategy aims to build the foundation for future operations that can more easily and quickly offset adversarial capabilities.
1. We refer to the proposed strategic approach as Offset-X to draw an analogy with the past three Offset strategies that the United States military pursued from 1950 to 2017 with great results. We chose to use X rather than Fourth Offset to ensure that our proposed actions are viewed as only a partial, not a comprehensive list of actions and whose attainment should be viewed as a temporary achievement that needs further revisions and updating.
2. Gray Zone Project, Center for Strategic and International Studies (last accessed 2022); China Cyber Threat Overview and Advisories, Cybersecurity & Infrastructure Security Agency (last accessed 2022); David Bandurski, China and Russia are Joining Forces to Spread Disinformation, Brookings TechStream (2022).
3. Critical infrastructure refers to those sectors that are considered so vital to the United States that their incapacitation, virtual or physical, would have a debilitating effect on national security, economic security, national public health or safety. See Critical Infrastructures Protection Act of 2001, 42 U.S.C. §5195c (2001).
4. 2021 Internet Crime Report, Federal Bureau of Investigation at 15 (2021).
5. Break Their Lineage, Break Their Roots, Human Rights Watch (2021).
6. Julian E. Barnes, et al., U.S. Intelligence Is Helping Ukraine Kill Russian Generals, Officials Says, New York Times (2022).
7. Benjamin Wittes & Gabriella Blum, The Future of Violence: Robots and Germs, Hackers and Drones, Basic Books at 311-352 (2015).
8. Nishawn S. Smagh, Intelligence, Surveillance and Reconnaissance Design for Great Power Competition, Congressional Research Service at 5, 7 (2020).
9. John R. Hoehn, Precision-Guided Munitions: Background and Issues for Congress, Congressional Research Service at 6-25 (2021).
10. Shaan Shaikh & Wes Rumbaugh, The Air and Missile War in Nagorno-Karabakh: Lessons for the Future of Strike and Defense, Center for Strategic and International Studies (2020).
11. Jack Detsch, Drones Have Come of Age in the Russia-Ukraine War, Foreign Policy (2022).
12. David Hambling, Failure or Savior? Busting Myths About Switchblade Loitering Munitions in Ukraine, Forbes (2022).
13. Jeffery Engstrom, System Confrontation and System Destruction Warfare: How the Chinese People’s Liberation Army Seeks to Wage Modern Warfare, RAND Corporation at 15-17 (2018). System destruction warfare includes but is not limited to the destruction of bases and carriers used for power projection — a move that was earlier associated with anti-access and area-denial thinking.
14. Ryan Fedasiuk, et al., Harnessed Lightning: How the Chinese Military is Adopting Artificial Intelligence, Center for Security and Emerging Technology at 38 (2021).
15. Xie Kai, et al., A Perspective on the Evolution of the Winning Mechanism of Intelligent Warfare, China Military Network – PLA Daily (2022).
16. Christopher Mihal, Understanding the People’s Liberation Army Rocket Force: Strategy, Armament, and Disposition, Military Review (2021).
17. Derek Solen, PLA Army Air Defense Units Improve Effectiveness, Resiliency, and Jointness, China Aerospace Studies Institute (2021).
18. John Costello & Joe McReynolds, China’s Strategic Support Force: A Force for a New Era, National Defense University (2018).
19. See e.g., Terri Moon Cronk, U.S. Forces Work With Partners in Numerous Military Exercises, U.S. Department of Defense (2017).
20. Testimony of Mark R. Cozad before the U.S.-China Economic and Security Review Commission, PLA Joint Training and Implications for Future Expeditionary Capabilities, RAND Corporation (2016).
21. Military and Security Developments Involving the People’s Republic of China, Annual Report to Congress, U.S. Department of Defense at 158 (2021).
22. Joint Operating Environment: The Joint Force in a Contested and Disordered World, U.S. Department of Defense Joint Staff (2016).
23. Mission Command: Insights and Best Practices Focus Paper, U.S. Department of Defense Joint Staff, Deployable Training Division at 3 (2020).
24. Mark Cozad, Toward a More Joint, Combat-Ready PLA, National Defense University Press (2019).
25. Jim Garamone, Ukrainian Resistance, Logistics Nightmares Plague Russian Invaders, U.S. Department of Defense (2022).
26. Chad Peltier, China’s Logistics Capabilities for Expeditionary Operations, Jane’s at 4 (2020).
27. Michael Tanchum, China’s New Military Base in Africa: What it Means for Europe and America, European Council on Foreign Relations (2021); Hal Brands, America and China Are in a Global Fight Over Military Bases, Bloomberg (2021); Where Are U.S. And Russian Military Bases In The World, RadioFreeEurope, (2015).
28. Dennis J. Blasko, Corruption in China’s Military: One of Many Problems, War on the Rocks (2015).
29. Thomas Carothers & David Wong, Authoritarian Weaknesses and the Pandemic, Carnegie Endowment for International Peace, (2020).
30. Caitlin Talmadge, The Dictator’s Army: Battlefield Effectiveness in Authoritarian Regimes, Cornell University Press (2015).
31. Feng Wang, et al., The End of China’s One-Child Policy, Brookings (2016); see also One-Child Policy ‘Weakens China’s Military,’ Radio Free Asia (2012); China Grappling with Effects of ‘One-Child Army’, Adds Unmanned Aircraft, Ballistic Missiles, Says Experts, Yahoo News (2021).
32. The United States Marine Corps Force Design 2030, intended to help prevent the People’s Liberation Army Navy from pushing past the First Island Chain, is a first effort to confront the PLA’s systems, rather than just close kill chains. SCSP Defense Panel Meeting (July 2022). For additional details, see Force Design 2030, U.S. Marine Corps (last accessed 2022).
33. Force Design 2030, U.S. Department of the Navy at 6 (2020).
34. U.S. Department of Defense Responsible Artificial Intelligence Strategy and Implementation Pathway, U.S. Department of Defense (2022); Kathleen Hicks, Deputy Secretary, Memorandum for Senior Pentagon Leaders on Implementing Responsible Artificial Intelligence in the Department of Defense, U.S. Department of Defense (2021); DoD Directive 3000.09, Autonomy in Weapon Systems, U.S. Department of Defense (2012).
35. Tony Ojeda, The Algorithm – Human Tasks vs Machine Tasks, District Data Labs (last accessed 2022).
36. Julie Obenauer Motley, The Testing and Explainability Challenge Facing Human-Machine Teaming, Brookings Tech Stream (2022).
37. What Is Computational Thinking?, Center for Computational Thinking, Carnegie Mellon University (last accessed 2022).
38. John Laird, et al., Future Directions in Human Machine Teaming Workshop, U.S. Department of Defense at 3 (2019).
39. OFFSET Swarms Take Flight in Final Field Experiment, Defense Advanced Research Projects Agency (2021).
40. Department of Defense Software Modernization Strategy, U.S. Department of Defense at 1-2 (2022).
41. Software Acquisition and Practices (SWAP) Main Report, U.S. Department of Defense, Defense Innovation Board (2019).
42. Department of Defense Software Modernization Strategy, U.S. Department of Defense at ii (2022).
43. Final Report, National Security Commission on Artificial Intelligence at 59-69 (2021); U.S. Department of Defense Responsible Artificial Intelligence Strategy and Implementation Pathway, U.S. Department of Defense (2022); Kathleen Hicks, Memorandum for Senior Pentagon Leaders on Implementing Responsible Artificial Intelligence in the Department of Defense, U.S. Department of Defense (2021); DoD Directive 3000.09, Autonomy in Weapon Systems, U.S. Department of Defense (2012).
44. DoD Instruction 3000.15, Plan Review and Approval Process, U.S. Department of Defense at 11 (2020).
45. For more details on the challenges related to the U.S. techno-industrial base and near-term recommendations, see Chapter 2 of this report.
46. Becca Wasser, Developing Integrated ISR Networks to Improve Coalition Responsiveness, Presented at SCSP Defense Panel Meeting (July 2022).
47. Summary of the Joint All-Domain Command & Control (JADC2), U.S. Department of Defense (2022).
48. Military-Civil Fusion and the People’s Republic of China, U.S. Department of State (2020).
49. Counter Autonomy: Executive Summary, U.S. Department of Defense, Defense Science Board at 3 (2020).